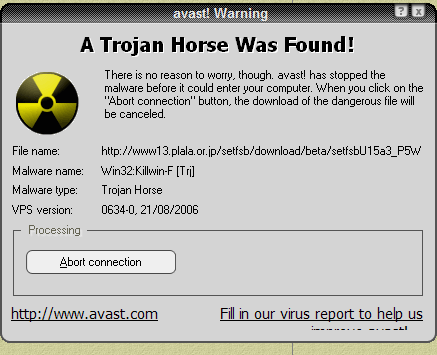
Spyware is a type of virus/malware which infects your pc stealthily without you knowing.
This information was collected from (1)
Spyware can come in a few different forms which depend on what the hacker is trying to get from your computer.
One of the forms of Spyware is the Trojan horse. The Trojan horse is a type of Spyware which disguises itself as a legitimate program like Java or Adobe flash player and infiltrates your computer. People usually don't take a second look at any programs which seem legit but that and a combination of other things costs almost 1 billion people $172 billion annually.

A different form of Spyware is called "System Monitors". System Monitors are usually disguised as freeware (free antivirus and software) which take note of everything you do on your computer. System monitors take note of your sent and received emails, keystrokes, websites visited and any programs that you run on your PC like microsoft word. This is used usually for ransom as any sensitive emails or programs are tracked by the owner of the system monitor.
Some less harmful forms of spyware are Adware and tracking cookies. Adware is usually put into your computer unknowingly via a Trojan and tracks what you search up to predict ads and sell you things that apply to you. Tracking cookies are pretty much the same as Adware, they also track what you search and forward that information to different websites to sell you certain products.
Identity theft is the process of fooling someone into thinking you are trustworthy or believable and letting them give you whatever you ask for like credit card information, emails, passwords and your social insurance number.
This information was collected from (2)
There are many types of identity theft that criminals use to steal your personal information such as: drivers license theft, mail identity theft, account takeover theft, synthetic identity theft, child identity theft and senior identity theft but I will be talking about the type of identity theft which are most prevalent in our society.
Synthetic identity theft is when a criminal (usually on the dark web) finds part of your identity online and adds new details to whatever they started off with to make a "new person" so to speak. A criminal could take your social insurance number and last name and make up an adress and first name (along with a phone number and plenty of other stuff) to make a new identity to sell on the dark web. If your SIN number was to get caught in this kind of identity theft your credit score could be ruined and you could have no chance of buying a house or any sort of big item for a long, long time.
Account takeover theft is when a criminal collects data which was leaked in a data breach from a large corporation and uses this data to log into your different accounts online and change them to their liking. Sometimes hackers could leak sensitive data from different companies and if that data is collected by the wrong people, your accounts could be breached. Any account ranging from your bank account to throw-away email account could be hacked.
Music piracy is when someone illegally downloads music off of the internet when it normally would cost money to listen to. Music piracy may not sound like a big crime that could get you into alot of trouble but in reality it costs the music economy 12.5 billion dollars each year and can get you up to 5 years of jail time and a $250000 fine.
Information for this article was collected from (4)
Information was also collected from (5)
People who pirate music usually get the music from hackers who run illegal websites and give away the music for free.
Also people usually dont think that music piracy is a big crime and that it wont be monitored by the police or some secret agency, but if you do it enough, the FBI or RCMP will fine you and potentially give you jail time.
All of the things I mentioned are the same for movie piracy but movie and tv piracy costs the industry anywhere from 29.8-71 billion dollars annually.
Cyberbullying is when people are bullyed by means of online voice calls or text chat. It may not sound like something that you should care about, but cyberbulying causes 41 suicides per year on average.
Information for this article was collected from (6)
More information was also collected from (7)
Cyberbullying is usually caused by a lack of empathy, boredom and the feeling that the person that is being bullyed deserves it.
Most cyberbullies are people who don't want to bully anyone in real life but think that they have anonymity through the web. They pose as someone who has no name and get inside other peoples heads to mess with them and bully them out of whatever they are doing.
A study done by Oxford University shows that cyberbullying any vulnerable youth multiplies the chance of them commiting suicide by 2.3. Cyberbullyed youth are also affected by mental health issues and self harm issues as well.
Cyberbullying has progressed to being a real problem in todays society since anyone can do anything to anyone else on the internet without consequence on their end unless what they do is devastating. For most cases of cyberbullying they are too small to be pursued by the police or other organizations.
I hope this article on the ethical issues related to computers was helpful and that this helped you learn more about different problems and viruses in the online world.
Here are my questions about the article:
1.What is a system monitor and what do they do?
2.How much does music piracy cost the music industry each year?
3.What were the results of the study done by Oxford University?
The answers to the questions are here